If you own any sort of digital assets like NFTs or crypto, then you have probably heard about Ledger hardware wallets. These wallets are said to be the safest way to store your digital assets—but can a Ledger wallet be hacked?
Can A Ledger Wallet Be Hacked?
Ledger wallets are built to withstand physical and software attacks. Its security chip means it’s resistant to malicious attacks like fault injections, laser attacks, electromagnetic tampering, and power glitches. Also, its BOLOS operating system keeps apps isolated to ensure private info remains secure.
Knowing the various ways a Ledger wallet could be compromised and how to avoid these various attacks is crucial to keeping your wallet and the assets within it safe. In this article, you’ll learn what to look out for and how to know if your wallet has been compromised.
How Can A Leder Wallet Be Hacked?
There are numerous ways that hardware wallets can be attacked. That being said, Ledger has done a great job covering all its bases to ensure these hacks don’t affect their devices. Here are some realistic ways a hardware wallet could be hacked, and how Ledger eliminates the threat.

1. Power Glitching
Power glitching can be used to violate a cryptographic coprocessor by disrupting the system and flooding the power supply of the hardware’s circuit board. If done correctly, this brief surge of power could lead to your wallet’s private info being exposed.
In order to execute this attack, a hacker would need physical access to your wallet.
Ledger’s Solution: By using a high-end security chip called a secure element (the same chip found in passports and credit cards), Ledger is resistant to this type of attack. Ledger wallets are the only hardware devices that use SE chips.
2. Side-Channel Attack
A side-channel attack (SCA) is an exploit hackers use to extract private info from a chip or system. This is done by analyzing various physical parameters such as supply current, execution time, and electromagnetic emission.
Hackers could potentially listen to the noise of the wallet while testing random PIN codes and also observing how each code changes the consumption behavior.
Since different PINs will leave a different footprints, hackers can determine which codes might work. Moreover, by watching the behavior of the power consumption with each attempt, hackers can build a database of information.
This database could then be used with a script that guesses PIN numbers one by one, eventually guessing the correct PIN.
Ledger’s Solution: In the case of a side-channel attack, Ledger’s secure element is able to safeguard against this type of attack as well.
3. Software Attack
A software attack is a direct hit on a device’s hardware security module (HSM). This module is responsible for safeguarding and managing digital keys, performing both encryption and decryption functions for digital signatures, and other cryptographic functions.
To attack the HSM, hackers need to have a better understanding of the technology than the developers themselves in order to locate vulnerabilities in the software’s code.
Carrying out this type of attack would require the hacker to plug in the hardware module to a computer to recover its underlying software. Then, after running a script that scans the code of the device, it locates the software in binary form—which only computers understand.
Of course, with a little finagling, hackers can transform the code into a human-readable form. From there, the goal is to find a vulnerability in the software so that the attacker can take control of the software and receive data from it.
Ledger’s Solution: The device’s BOLOS operating system keeps apps isolated to ensure private info remains secure. That means if you were to download an app that had malicious intent, there’s no way it could gain access to the private information that’s stored on your Ledger device.
4. Phishing Link Scam
Perhaps the most common type of scam that is experienced in the web3 space is accomplished via a phishing link. These links lead to malicious websites that are designed to gain access to your wallet.
Generally, visiting this type of website isn’t enough to get your wallet compromised. Instead, scammers will create a website that looks like a popular and trusted website (such as a well-known NFT marketplace) or offer you a deal that’s too good to pass up.
Then once you go to sign the transaction using your wallet, you actually voluntarily sign over your access to the attacker. From there, the scammer swiftly sends all your digital assets to their own wallet so that they can liquidate them for a quick profit.
The worst thing about this common NFT scam is that it usually goes unnoticed, that is, until it’s too late and you realize your wallet has been drained. To make things worse, hackers don’t need physical access to your Ledger device to accomplish this attack.
All they need is for you to get online, click on their link, and then sign a transaction using your wallet.
Ledger’s Solution: Since Ledger hardware wallets store all of its sensitive information offline and on the device itself, there is little concern for this type of hack. However, if you decide to connect your wallet to a malicious site and voluntarily sign over control, there’s very little that can be done at that point. That’s why it’s important to stay vigilant and consider getting a second wallet (one for transactions and one for storage).
How Secure Are Ledger Wallets?
Ledger devices are the most secure wallets on the market. By using a combination of a secure chip (the same technology found in credit cards and passports) and its one-of-a-kind BOLOS operating system, Ledger wallets are protected from malicious attacks including software, side-channel, and glitches.

To further elaborate on just how secure Ledger devices are, let’s break down each security measure.
Password
Let’s start with the basics. All ledger wallets require you to set up a password so that you can lock it to prevent unauthorized access. The password encrypts all your sensitive user data such as your account names, public addresses, and your transactions.
To ensure your password remains secure, it should be a mix of upper and lower-case characters.
PIN Code
Ledger’s PIN code contains 4 or 8 digits chosen by you when you first set up the device. This adds another layer of protection by preventing unauthorized access to your digital assets. You can always change your PIN code at any time.
Secret Phrase
If you aren’t aware, nearly every crypto-based wallet comes equipped with a secret phrase (also called seed phrase, private key, and recovery phrase). This phrase is the literal key used to access your wallet. Even if you forget your password, you can use your wallet’s recovery phrase to regain access and create a new password.
Most wallets come standard with a 12-word secret phrase, however, Ledger wallets come with a 24-word phrase. But, how secure can this phrase really be? Extremely secure.
Ledger uses a standard called BIP-39 to generate every single one of their wallet’s secret phrases. This standard consists of only 2,048 words from the BIP-39 wordlist.
That being said, there are 115,792,089,237,316,195,423,570,985,008,687,907,853,269,984,665,640,564,039, 457,584,007,913,129,639,936 possible mnemonic seeds.
How’s that for security?
Secure Chip (secure element)
Ledger’s secure element is a step up in terms of security. A secure chip is the same technology that’s found in your passport, credit cards, and SIM cards. Its sole function is to protect highly sensitive information from being accessed by people with malicious intent.
BOLOS Operating System
Ledger’s very own BOLOS operating system is unique to their devices. Similar to more familiar operating systems like Windows and Mac OS, BOLOS enables Ledger wallets to install applications that are isolated from each other. Furthermore, it also ensures your 24-word secret phrase remains isolated from the applications on the device.
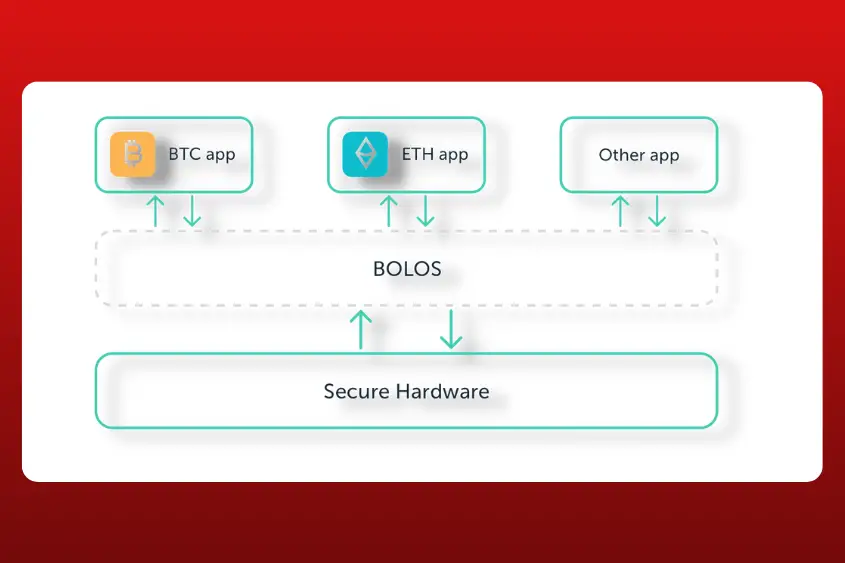
As shown in the image above, applications can’t interact with each other. Instead, they communicate directly with BOLOS. This keeps malicious users and developers away from your private info.
With that, third parties can still develop applications for Ledger devices. Of course, there’s still a process in place for being accepted as an official app on Ledger Live.
How to Know if Your Ledger Wallet Is Compromised
Even though it’s apparent that Ledger provides the safest NFT wallet on the market, it’s still possible that your wallet could be compromised. Below are a few steps to check that your wallet isn’t compromised.

1. Know where your device came from
The first step is to confirm that you ordered your device directly from Ledger. Ordering your wallet from resellers such as Amazon, eBay, or from friends on the internet is a bad idea as your device could arrive compromised.
2. Verify the box contents
Every Ledger box should contain the proper contents. If an item is missing, this should be a major red flag that your wallet may have been accessed by someone else. The box contents are as follows:
- Ledger Wallet
- USB Type-C cable
- An envelope containing:
- Get Started leaflet
- Care and Regulatory Statement
- 3 Recovery sheets
- Accessories:
- Keychain
- Packaging:
- Ledger-branded cardboard box and sleeve
3. Ensure the recovery phrase hasn’t been setup
Your recovery words are generated on your Ledger wallet screen in the initial setup. If your device came with a pre-filled recovery sheet or if your wallet did not generate recovery words during setup, your device is not safe to use.
4. Check for factory settings
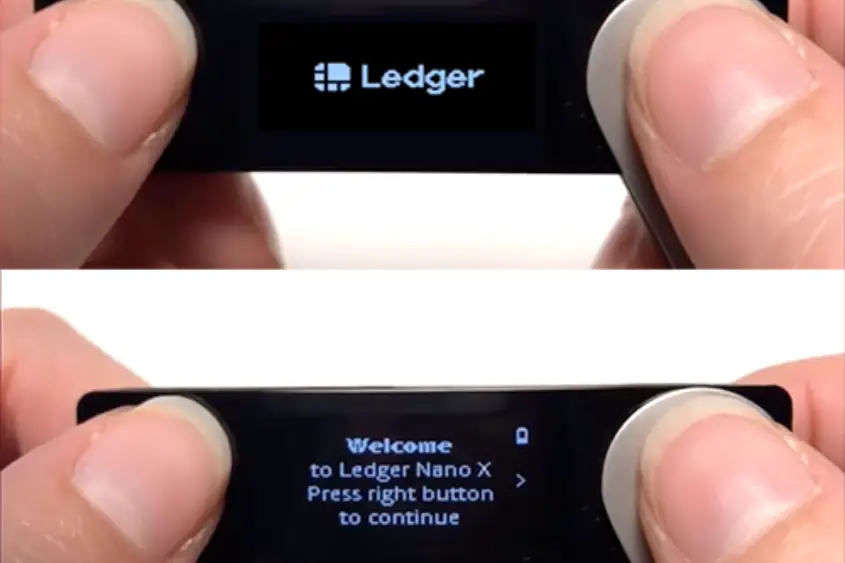
The factory settings on every new Ledger device should be the same. When your first turn your wallet on, it should display the Ledger Logo. Once you release the buttons used to turn it on, the welcome message should appear—prompting you to press right to continue.
The next step is to set up your PIN code. It’s important to note that Ledger does not provide you with a PIN, you are responsible for entering your own. So if your wallet requires a PIN code the first time you use it, it’s not safe to use.
5. Confirm authenticity with Ledger Live
Your last line of defense to ensure your Ledger wallet has not been compromised is to confirm its authenticity using Ledger Live.
Only genuine Ledger devices hold a secret key that is set during the manufacturing process. Ledger Live uses this key to pass the genuineness check. If your device doesn’t pass, don’t use it.
6. Check hardware integrity (for advanced users only)
If you’re someone who enjoys taking things apart and putting them back together, then you might want to consider checking your wallet’s hardware integrity.
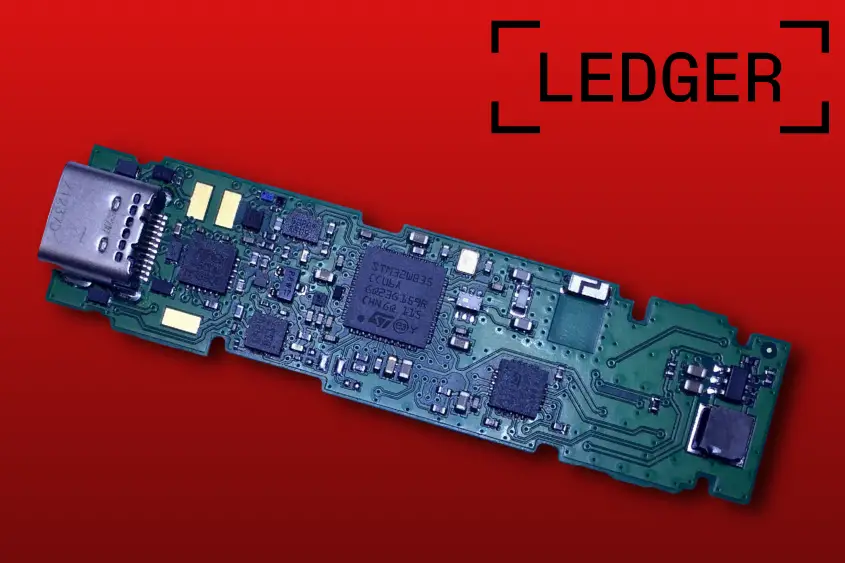
To do this, you can open your device to verify no additional chip has been added. Just make sure you are aware of all of Ledger’s hardware revisions before jumping to any conclusions about whether or not there’s an additional chip.
If you have reason to believe that something doesn’t look right, don’t use your device, and contact Ledger immediately.
Tips for Keeping Your Ledger Wallet Safe
Ledger’s team of over 130 employees who have extensive knowledge in embedded securities, cryptocurrency, and NFTs, have done everything in their power to develop the most secure wallet for safely storing your digital assets.

That being said, it’s up to you to ensure that you’re doing everything in your power to keep your wallet safe. Below of some of my top safety tips to ensure your wallet remains secure.
1. Store your Ledger device and private info in a secure location
The safest place to store your wallet and private info such as your recovery phrase, password, and PIN code is in a secure location, such as a fireproof safe.
You should never store your wallet’s private information on your computer or anywhere online, as it increases the likelihood of your wallet being compromised.
Writing your phrase down using a pen and paper is the most common practice. However, you risk losing your phrase if the paper were to somehow get destroyed—such as in a fire or flood.
For this reason, I recommend picking up a stainless steel seed storage plate. These plates are fire and waterproof and come with an engraving pen to easily record your phrase.
2. Only buy your wallet directly from Ledger
There’s no reason to purchase your wallet from anywhere but from Ledger directly. Under no circumstances should you trust buying a wallet from someone else or on Amazon.
I have seen numerous people buy compromised Ledger wallets from Amazon, and it’s not pretty. Once you receive it and fill it with your assets, the seller will drain your wallet. Trust me. It’s worth spending the extra $10-$20 to ensure you are buying a legit wallet that you can trust.
3. Create a strong password
Even though your secret phrase is one of your wallet’s greatest lines of defense, it’s best to create a strong password too.
A strong password includes upper and lowercase letters, numbers, and symbols. Also, it’s best to not use words when creating a password. Rather, choose random characters that make your password near impossible to guess.
4. Do not connect your Ledger wallet to the internet
The most common scam in the NFT and crypto space is phishing links. If you plan on using your wallet as a storage solution for your NFTs, crypto, and other digital assets, then you should not connect it to the internet.
The greatest strength of a hardware wallet like Ledger is that all your wallet’s private info is stored offline. However, the moment you decide to connect it to the internet, you lose that benefit. All you’re really doing is putting your wallet and the assets within it at risk.
If you fall victim to a fishing link scam, there’s very little that can be done to recover your assets.
5. Keep your wallet locked when not in use
There’s no reason to keep your wallet unlocked if you’re not actively using it. Every time you are done with it, even if you’re only stepping away for a minute, make sure to lock it.
It only takes two seconds and it puts up another barrier to protect against hackers. Once you’re ready to use it again, you can easily unlock it using your PIN and password.
Ultimately, just about any type of device can be hacked. However, Ledger has done everything they can to ensure its wallets are the most secure device on the market for safely storing your digital assets, and for a very reasonable price. If you own any NFTs, crypto, or other blockchain-based assets, then you need to get a Ledger.

7 thoughts on “Can A Ledger Wallet Be Hacked? (+ Tips to Keep it Safe)”
Comments are closed.