Hardware wallets are known as the most secure way to store crypto assets in modern-day society. If you’re new to the world of crypto or hardware wallets in general, you might be wondering: can you trust hardware wallets?
Yes, you can trust hardware wallets to securely store your digital assets. Over 5 million people worldwide use crypto wallets to keep their private keys offline and reduce the risk of theft. A trustworthy wallet has multiple security features including a secure chip, biometrics, and PIN codes.
Of course, not all hardware wallets are created equally. Let’s delve deeper into this topic. Here is what you will learn:
Contents
Can You Trust Hardware Wallets?
In general, a considerable amount of people trust hardware wallets to secure their digital assets. According to Tech Crunch, two prominent hardware wallet companies Ledger and Trezor have amassed more than 5 million users alone.
As if that number isn’t impressive enough, look at this!
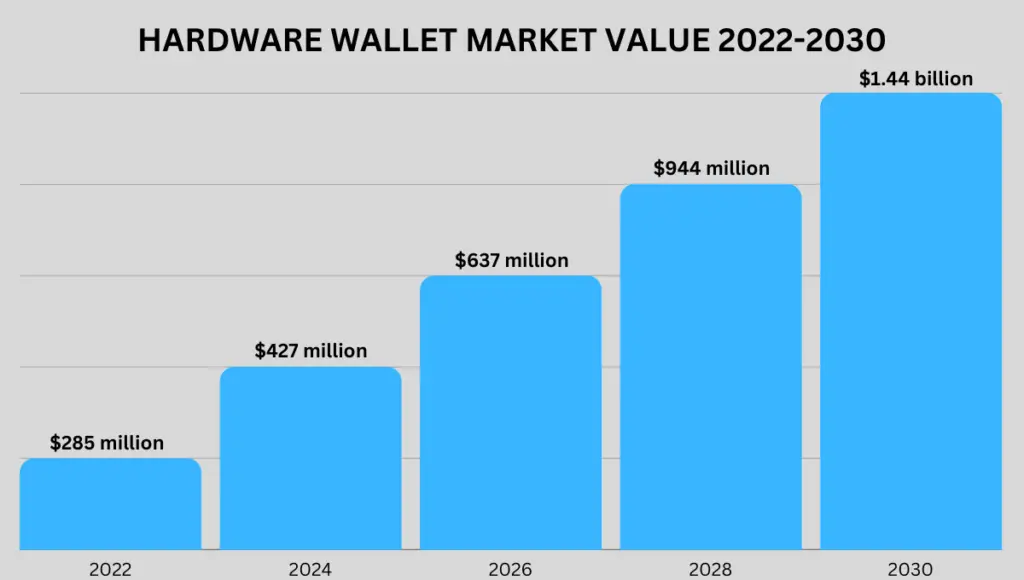
In 2022, the hardware wallet market was valued at $285 million.
The market is expected to reach more than $1.44 billion by 2030, with a compound annual growth rate of 22.5% according to Market Research Future.
So yes, there are millions of satisfied users who trust hardware wallets to secure their assets which are worth thousands to millions of dollars, per individual.
In fact, I’ve been using my Ledger hardware wallet for several years without any issues. I currently store my most valuable NFTs and crypto in my device, and I trust it to do its job.
Nevertheless, there are various factors to consider before determining if a particular hardware wallet can be trusted or not.
What to Look for When Choosing a Trustworthy Hardware Wallet

Here is what to look for when choosing a trustworthy hardware wallet.
Security standards: Any quality hardware wallet you buy should have a long list of security features.
Ensuring these features are present in the device can help you determine how trustworthy a wallet might be.
Some essential security features include:
- Secure chip element
- Unique operating system
- Consistently updated firmware
- Software-based asset management system
- Biometric authentication
- Air gap technology
Security features will vary for each brand and model of hardware wallet you look at.
However, it’s important to check that the device has at least a few of these features to ensure optimal security.
Solid reputation: We live in a world where reviews can make or break a business and its reputation.
Fortunately, that means you can get a good idea of the quality of a hardware wallet before you purchase it.
By looking at honest user reviews, you can quickly determine the market sentiment towards a particular hardware wallet brand or a specific model.
If the general consensus is negative, avoid that wallet. If the overall outlook seems positive, you can assume a majority of users are satisfied with the product and trust it to secure their crypto assets.
Some of the most reputable hardware wallet brands include:
But, you don’t have to take my word for it.
Please, always do your own research. Even if a particular hardware wallet company is trustworthy, you might prefer the features another brand offers.
Third-Party Audits: Most reputable hardware wallet manufacturers have undergone third-party audits to verify the security of their devices.
These audits can provide additional reassurance when purchasing a hardware wallet.
Here are some hardware wallet brands that utilize individual and third-party audits:
- Ledger
- Trezor
- Keystone
- BitBox
I know what you’re thinking: “Great, but have any of these hardware wallets ever been hacked?”
And to be honest, some of them have.
Here is a list of hardware wallet brands—some of which have been hacked.
| Hardware Wallet Brand | Has Been Hacked | Type of Hack | Last Hacked | Security Concerns Fixed |
|---|---|---|---|---|
| Ledger | Yes | Cyberattack: This server breach leaked approximately 1 million users’ emails. It was not a wallet hack. | July 2020 | Yes, Ledger’s servers have since been upgraded to prevent |
| Trezor | Yes | Fault Injection Hack: Professional hacker, Kingpin, surpassed security microcontrollers to access a wallet’s PIN code to recover lost assets. | January 2022 | Yes, Trezor has since upgraded microcontrollers to prevent this type of hack from reoccurring. |
| Keystone | No | No hack has been publicly reported with the Keystone hardware wallet. | N/a | Currently, there are no security concerns to address. |
| BitBox | No | No BitBox wallets have been hacked. However, a wallet hacker named Lazy Ninja did discover a side-channel attack vulnerability. | November 2018 | According to ShiftCrypto, BitBox is still vulnerable to non-invasive, side-channel attacks. |
| Ngrave | No | No hack has been publicly reported with the Ngrave hardware wallet. | N/a | Currently, there are no security concerns to address. |
Why Should I Trust Hardware Wallet Firmware?
It’s not advantageous for hardware wallet manufacturers to create faulty firmware deliberately, even if they think it wouldn’t be detected easily. Such actions would lead to reputational damage, legal repercussions, and loss of customer trust, which would harm their business in the long run.
Hardware wallet manufacturers have a vested interest in maintaining the integrity of their products and providing secure storage solutions for their customers.
After all, this is the core value proposition of their business.
Thus, it’s highly unlikely that any reputable hardware wallet manufacturer would deliberately create faulty firmware.
Furthermore, companies like Trezor ensure their firmware remains open source—meaning anyone can examine the firmware to check for vulnerabilities.
That said, there are pros and cons to the firmware being open source including.
Open source pros:
- Transparency: Open-source software enables anyone to inspect the code which can increase trust in the security and privacy of the device.
- Community review: Open source software is open for review by the entire community of developers. This can result in more robust and secure code.
Oftentimes manufacturers have a bounty for any developer that uncovers a vulnerability, thus acting as an incentive.
- Customizability: Developers can modify and improve the code to suit their specific needs, which can lead to the creation of new features and functionality that might not have been thought of by the original team.
- Collaboration: The open nature of the code can encourage collaboration among developers, which can result in a more secure and user-friendly device.
Open source cons:
- Complexity: Open-source software can be more complex and difficult to navigate than closed-source software.
This can make it harder for non-technical users to understand and use. That said, non-tech folks probably don’t care to read code anyways. - Security risks: Because the code is open and available to everyone, it can potentially be exploited by malicious actors who find vulnerabilities in the code.
This is arguably the greatest concern—but also the greatest aspect of open-source software. - Support and maintenance: There may not be a single company responsible for supporting and maintaining the software, which can make it harder to receive help if issues arise.
In my experience, this has not been the case with hardware wallet companies though. - Forking: Open-source software can be easily forked, meaning different versions of the same software can exist potentially causing confusion and fragmentation.
As a result, bad actors are more likely to create a malicious version of the software. That’s why it’s important to always double-check the site you’re connecting to before downloading any firmware updates.
Not all trustworthy hardware wallet companies are open-source though. For example, Ledger wallets are closed-source.
However, the apps on Ledger Live remain open-source.
But, even closed-source firmware can have vulnerabilities.
In 2018, a vulnerability was discovered in the Ledger Nano S that could have allowed an attacker to steal cryptocurrency from the device.
However, it was determined that the vulnerability was not critical and was rather impractical.
Besides, any reputable hardware wallet manufacturer takes security very seriously and releases regular updates to their software as soon as vulnerabilities are discovered.
Knowing that it’s important to keep your hardware wallet software up-to-date to ensure that you have the latest security patches.
Can You Lose Assets In a Hardware Wallet?
The only way you could lose assets in a hardware wallet is if you lost access to your wallet, and didn’t have the recovery seed phrase. Because crypto assets are stored on the blockchain and not in your wallet, you can always access them using another device.
Your recovery phrase is a sequence of words that are generated when you set up your hardware wallet.
It’s essential to keep this phrase safe, as it’s the only way to recover your assets.
If you’re worried about losing your assets, you should consider having a backup hardware wallet on-hand and ready to go.
This will allow you to recover your assets quickly in case of an emergency and transfer them to a new wallet address.
What If a Hardware Wallet Company Goes Out of Business?
Hardware wallets are designed to be independent of the company that makes them. So even if the company goes out of business or stops supporting the wallet, you can still access your funds. Remember, your private keys are stored on the device itself, not on the company’s servers.
Moreover, nearly all hardware wallets on the market generate their recovery seed phrase using the BIP-39 wordlist.
This is simply a specified list of over 2,000 words used to generate wallet seed phrases.
That means as long as you have access to a wallet that utilizes this list, you can access your funds.
I want to make this very clear. You don’t need to use the same hardware wallet or even brand of wallet to access your funds on the blockchain.
Your wallet’s seed phrase can be used on any device that supports the BIP-39 wordlist—assuming your initial wallet utilized this list.
What Is the Safest Hardware Wallet?

The safest hardware wallet is the Ledger Nano X. It has no public report of being hacked and it uses various security components to keep your crypto safe. Components include a secure chip element and a proprietary isolated operating system used to prevent both physical and digital attacks.
I’d be lying if I said the Ledger Nano X was the only safe hardware wallet though.
There are several trustworthy brands all with unique devices that I consider safe.
You can check out my complete list of the safest hardware wallets here.
Frequently Asked Questions
Are hardware wallets 100% safe?
No crypto wallet is 100% safe. However, by using a reputable hardware wallet in conjunction with the best wallet practices, you can prevent 99.9% of hacks and scams from affecting you or your assets.
What is the most trusted hardware wallet?
The most trusted hardware wallet is the Ledger Nano X. With over 3 million devices sold worldwide, there’s no doubt that a majority of crypto enthusiasts trust the Ledger Nano X to keep their assets secure. Plus, there have been no reported vulnerabilities with it.
Why is a hardware wallet safer than a mobile wallet?
It’s simple. A hardware wallet stores its private key offline on the device itself. A software wallet stores its private key on the software which is connected to the internet. Thus, hardware wallets are less vulnerable to various physical and digital hacks, as well as popular scams.
