There are several types of crypto wallets for storing your digital assets. Of course, consumers are always in search of the most secure solution.
In your quest for security, you might have come across air-gapped wallets. So, what is an air-gapped hardware wallet?
Air-gapped hardware wallets are completely isolated from the internet and other communication technologies. This includes Bluetooth, WiFi, NFC, and USB cables. Transactions are completed using QR codes or SD cards, reducing the risk of compromise. Nonetheless, air-gapped wallets can still be hacked.
There is plenty more to cover regarding air-gapped wallets. Here is what you will learn.
Contents
If you prefer to listen, we covered this topic on our podcast as well.
What Is an Air-Gapped Hardware Wallet?

Air-gapped hardware wallets are similar to any other hardware wallet.
The only real difference is that air-gapped devices lack the ability to connect to the internet or other external devices such as your computer.
This is done to limit exposure to potential hackers that could use these common forms of communication to compromise your crypto wallet.
How Do Air-Gapped Wallets Work?
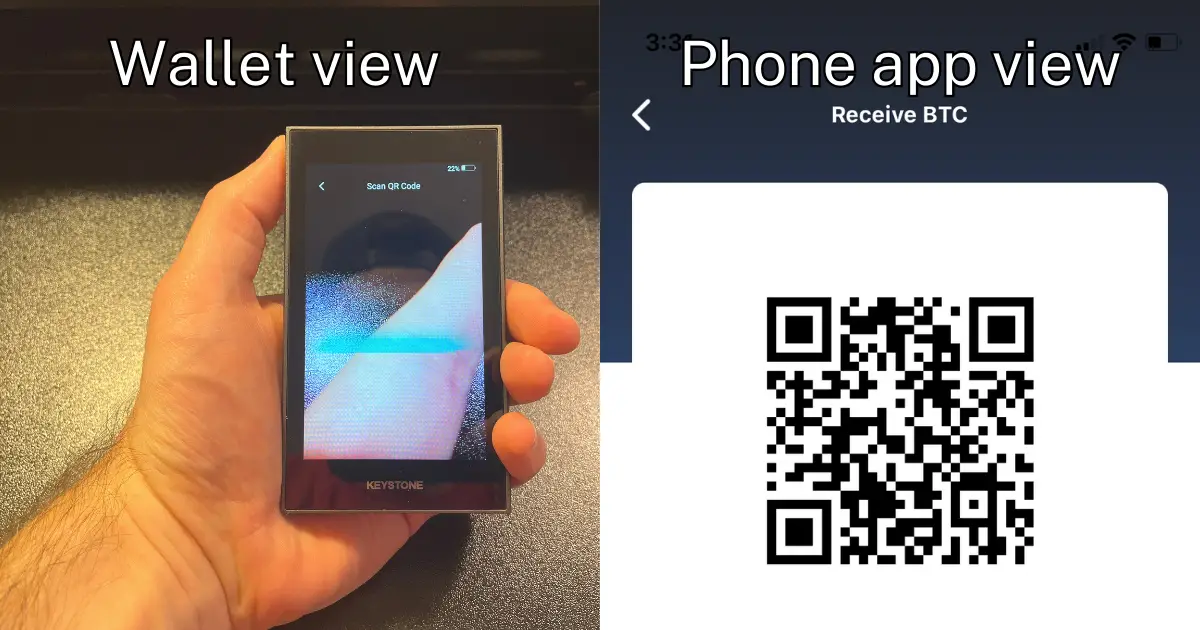
Air-gapped wallets utilize QR codes or SD cards to initiate and complete transactions on the blockchain. This eliminates the risk of compromise while still enabling the user to manage their funds in a secure and efficient manner.
Here is how air-gapped wallets work.
Initiate and approve transactions via QR codes
QR codes are often used to manage funds and transact when using an air-gapped cold-storage wallet.
Generally, a transaction request is initiated on an internet-connected device like your computer or smartphone.
This action then generates a QR code you have to scan using your hardware wallet to approve the transaction.
Once scanned, you’re required to verify the transaction details on the screen of your hardware wallet.
If everything appears correct, you can confirm the transaction using your wallet.
This process is done entirely offline, which means it is highly secure and virtually immune to potential malicious attacks.
Initiate and approve transactions via an SD card
SD cards are also used to initiate and verify transactions when using an air-gapped wallet.
Similar to the QR code method, the transaction request is initiated via a device that is connected to the internet. From there, you have to save the transaction details onto an SD card.
That SD card is then inserted into the hardware wallet where it prompts you to verify and approve the transaction details.
Both of these methods reduce the overall risk of being hacked. But, does that mean air-gapped wallets are completely immune to hacks and scams?
Are Air-Gapped Hardware Wallets Safe?
Air-gapped hardware wallets are safer than non-air-gapped wallets. They keep your private keys and transactions offline. But even air-gapped wallets have minor interactions with internet-connected devices like computers. As a result, these wallets are not completely immune to hacks or scams.
Despite air-gapped wallets being the safest crypto wallets on the market, they are still susceptible to malicious attacks.
Here are some ways an air-gapped wallet could be compromised.
Installing malware on your SD card
Despite air-gapped wallets being largely isolated from external devices, they are still exposed to malware via the SD card.
An SD card isn’t only used to initiate and complete transactions, but it can also be used to update the device’s firmware.
Hence if a hacker were to install malicious code onto the SD card while it’s connected to your computer, they could potentially compromise your wallet once you insert it back into the device.
To avoid unknowingly installing malware on your wallet, here are some precautions.
- Use a quality hardware wallet that you bought directly from the manufacturer. Preferably one that has been audited for security (i.e. don’t purchase your wallet on eBay).
- Use a brand-new SD card in conjunction with your hardware wallet.
- Regularly updated the hardware wallet’s firmware to patch any known vulnerabilities. Always verify you are visiting the correct URL before downloading any firmware updates.
- Store your hardware wallet and SD card in a secure location. Avoid using the SD card for anything but your hardware wallet.
- Have a dedicated computer that you use only for transacting with your hardware wallet. If you don’t have the means to own a dedicated computer, at least run a malware scan on your computer once per month (you can use a free scanner like MalwareBytes).
QR code substitution hack
QR codes are arguably more secure than other communication channels like Bluetooth or USBs, but they still pose a threat to your wallet’s security.
Although not as common as other hacks, a QR code substitution attack replaces the legitimate QR code with a malicious one. This could be achieved if the hacker were to gain access to your computer or smartphone.
The attacker could then replace the legitimate QR code with their own, which would direct the transaction to their own address.
Also, malicious code could place a partially signed transaction (PSBT) on your device. This is mainly a threat if transacting on the Bitcoin blockchain as it utilizes PSBTs.
To execute a partially signed transaction, the hardware wallet would need to complete the missing signatures.
If a malicious QR code included a partially signed transaction with a missing signature, the hardware wallet could potentially complete the transaction without the user’s knowledge or consent.
So how do you avoid malicious attempts via QR codes? Here are our best tips.
- Verify the QR code source: Only scan QR codes generated by a trusted source. The only QR codes you should be scanning will be generated by your wallet’s portfolio management app or a third-party software wallet.
- Verify the transaction details: Check that the transaction details displayed on your hardware wallet match the details in the QR code. Ensure the amount, address, and other details are correct before authorizing the transaction.
- Enable additional security features: Some hardware wallets offer extra security features. Such features display a message confirming the transaction details before it is sent or require physical authorization to confirm the transaction.
I wanted to highlight these potential concerns not to scare you, but to inform you that there is still a risk even if using an air-gapped, cold-storage wallet.
Pros of Air-Gapped Wallets
Reduced risk of phishing attacks
Because air-gapped wallets are unable to connect to the internet or any devices that utilize the web, the likelihood of falling victim to phishing scams is slim.
Reduced risk of data leakage
Air-gapped hardware wallets do not transmit data over the internet or Bluetooth, which reduces the risk of data leakage or interception.
Increased security
Air-gapped wallets provide a higher level of security compared to non-air-gapped wallets because it keeps your private keys offline while also eliminating external communications that pose a threat.
Cons of Air-Gapped Wallets
Requires additional hardware

Certain devices might require additional hardware. This adds to the overall cost of using an air-gapped wallet.
For example, the Keystone Pro wallet I use is 100% air-gapped, but it doesn’t come with the required SD card and card reader to install the firmware updates.
Fortunately, this additional hardware doesn’t cost much extra (about $15) but it’s an inconvenience nonetheless.
Potentially creates a false sense of security
One of my main concerns regarding air-gapped wallets is that users will completely disregard hardware wallet best practices because they think their wallet is untouchable.
As you now know, there are obvious pros to using an air-gapped hardware wallet. But they aren’t impenetrable. If you aren’t careful, your digital assets could still be compromised.
Frequently Asked Questions
Is Ledger air-gapped?
None of Ledger’s wallets are air-gapped. They all either use a Bluetooth connection or a USB cable.
What is the best air-gapped hardware wallet?
The best air-gapped hardware wallet is the Keystone Pro. It’s 100% air-gapped and utilizes QR codes to initiate and approve transactions. Not only is it one of the most secure crypto wallets, but it’s also affordable costing only $169.
Are air-gapped wallets better than non-air-gapped wallets?
Air-gapped hardware wallets offer more security than non-air-gapped wallets. However, non-air-gapped wallets might be preferred by some users due to their convenience. However, considering air-gapped devices are equally as affordable as any other device, they’re a no-brainer if you’re concerned about security.
What is air-gapped cold storage?
Air-gapped cold storage refers to a hardware device that stores your private keys offline and is completely isolated from the internet. Air-gapped cold storage is one of the most secure ways to store your digital assets like crypto and NFTs.
