You’ve heard that a hardware wallet is the most secure way to store your crypto assets. But, can hardware wallets can be hacked?
In this complete guide you will learn:
Can Hardware Wallets Be Hacked?
Reputable hardware wallets like Ledger and Trezor are almost impossible to hack. Most hardware wallets use multiple security components including secure chips, isolated operating systems, PIN codes, and passwords making them resistant to both digital and physical attacks.
While reputable hardware wallets like Ledger and Trezor are extremely difficult to hack, no device is entirely immune to potential security breaches.
As with any electronic device, hardware wallets are susceptible to vulnerabilities that can be exploited by sophisticated hackers. In some cases, hackers use social engineering techniques like phishing and malware to compromise hardware wallets.
Additionally, hardware wallets can be physically tampered with, or their firmware can be altered by attackers.
Despite these potential vulnerabilities, hardware wallets remain one of the most secure options for storing cryptocurrency. By following best practices like keeping your device updated and using strong passwords, you can greatly reduce the likelihood of a successful attack.
In my experience, one of the best ways to ensure your hardware wallet can’t be hacked is to buy one from a trusted brand.
Also, there are plenty of other tactics to help keep your wallet safe that we’ll talk about below.
Are Hardware Wallets Unhackable?
Hardware wallets are not entirely immune to hacking, but they are much more secure than software wallets. They store private keys, passwords, and PIN codes offline using secure chip technology and custom operating systems, making them less vulnerable to most types of hacks.
While hardware wallets are generally considered to be one of the most secure ways to store cryptocurrency and other blockchain-based assets, it’s important to remember that they are not completely invulnerable to hackers.
Sophisticated hackers have been known to use advanced techniques like side-channel attacks or power glitching to bypass the security measures of some hardware wallets.
However, these types of attacks are relatively rare, and most hardware wallets have safeguards in place to prevent them.
By taking proper precautions, like keeping your device in a safe location and avoiding third-party apps or unsecured networks, you can greatly reduce the risk of a successful attack on your cold-storage wallet.
How to Hack a Hardware Wallet
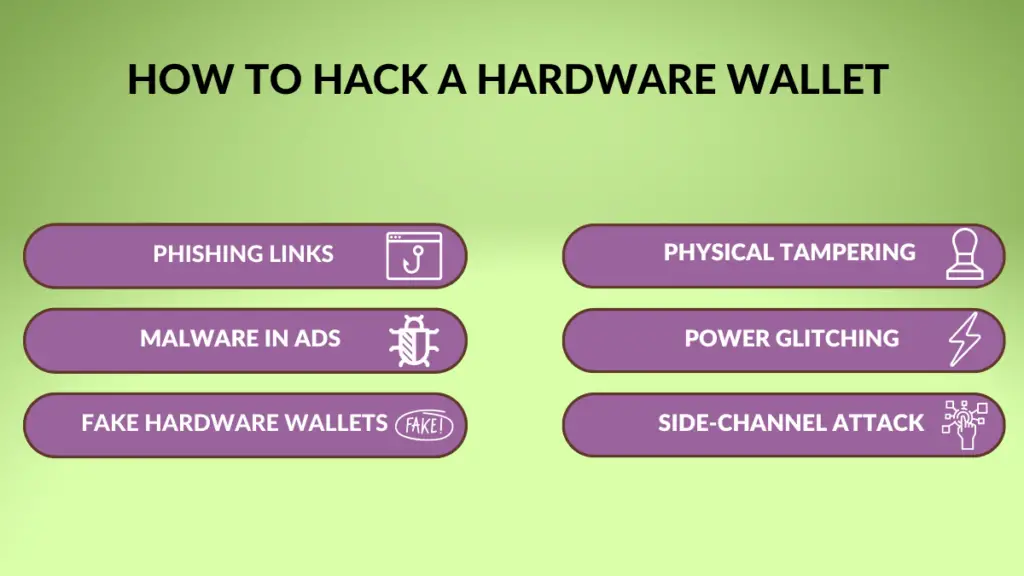
Phishing links
Phishing links are used to trick users into giving up their seed phrase or private key by posing as legitimate crypto companies or support teams. Once the attacker has obtained this information, they can use it to gain access to your hardware wallet and steal your funds.
To avoid falling victim to phishing attacks, never enter your seed phrase or private key into a website or app. Hardware wallet companies and other legitimate companies will never ask for your seed phrase or private key, so be cautious of any request for this information.
This is by far the most common scam in the crypto realm right now.
Malware in Ads
Malware ads are a sneaky way hackers inject malicious code into online ads to infect your computer or device with malware. This attack can compromise the security of your hardware wallet if you accidentally click on an infected ad while browsing a website that promotes hardware wallets.
To protect yourself against malware ads, use an ad-blocker extension in your web browser or avoid clicking on ads altogether.
When shopping for hardware wallets, only visit trustworthy websites and take the time to verify the legitimacy of both the website and the hardware wallet manufacturer before making a purchase.
Undoubtedly, malware ads are a common scam in the crypto space. Even prominent thought leaders, like NFT God, have been hacked.
Counterfeit hardware wallets
Counterfeit hardware wallets are created by scammers and sold through third-party sellers or on auction websites like Amazon and eBay. These counterfeit wallets appear identical to the real ones but are pre-loaded with malware that steals your private key and seed phrase.
To avoid falling victim to counterfeit wallets, always purchase them directly from the official manufacturer or authorized resellers. Check the hardware wallet’s packaging and features against the official website to ensure it is genuine. Never buy a hardware wallet from an untrusted source or one that has already been opened.
If you’re considering purchasing one of the two most popular hardware wallets, it’s important to be able to spot fake versions of these wallets.
Both wallet companies provide useful resources to help you identify a fake.
Check out Ledger’s guide and Trezor’s guide to spotting a fake wallet to ensure you’re buying a genuine product and protecting your cryptocurrency investments.
Physical tampering
Physical tampering involves an attacker gaining access to your hardware wallet and modifying it in a way that allows them to steal your private key or seed phrase. This can be done by opening the device and modifying the hardware or firmware to extract the information, or by using sophisticated tools to probe the device and obtain sensitive information.
To protect your hardware wallet from physical tampering, always keep it in a secure location and be wary of anyone who asks to borrow or access it.
Power glitching
Power glitching is a method of exploiting a hardware wallet’s vulnerability to electrical fluctuations in order to bypass its security measures and gain access to the user’s private keys. This attack involves manipulating the device’s power supply to induce a glitch or error in its operation, which can cause it to leak sensitive information.
Using a high-quality hardware wallet from a reputable manufacturer, like Ledger, that’s designed to withstand power fluctuations is the best way to avoid this type of hack.
Also, be careful when using USB cables or power adapters that are not provided by the manufacturer, as these can introduce voltage fluctuations that may compromise your hardware wallet’s security.
Side-channel attack
A side-channel attack targets the physical vulnerabilities of a hardware wallet, such as electromagnetic emissions or power consumption patterns, to extract sensitive information from the device.
Unlike other hacks, side-channel attacks don’t rely on breaking the device’s cryptographic algorithms.
To safeguard against these attacks, use a hardware wallet that is built to resist them, such as a device that has a secure element or a multi-layered security architecture.
To maintain your wallet’s security, ensure that you regularly update its firmware to include any security patches that the manufacturer has released to counter new types of attacks.
Why Hardware Wallets are Better than Software Wallets
Hardware wallets are better than software wallets because they provide enhanced security through offline storage, hardware encryption, and multi-layered authentication. Unlike software wallets, hardware wallets can protect your assets against keylogging, phishing, and other types of online attacks.
They also eliminate the risk of losing your private keys due to a computer crash or other technical issue. With hardware wallets, you have full control over your digital assets and can keep them safe from potential security breaches.
Of course, there are pros and cons to both hardware and software wallets.
Hardware (cold-storage) wallet pros and cons
Pros:
- More secure than software wallets
- Can be used to securely store multiple cryptocurrencies
- Offline storage protects against online attacks
- Easy to use and set up
- Typically come with a backup and recovery feature
Cons:
- Can be expensive
- Not as convenient to access as software wallets
- Can be lost or damaged, leading to the loss of funds if not properly backed up
- Some models have limited storage capacity
- May require firmware updates to remain secure over time
Software (hot) wallet pros and cons
Pros:
- Convenient and easy to use
- Often free to download and install
- Can be used on a variety of devices, including mobile phones and computers
- Can be more accessible for beginners
Cons:
- Less secure than hardware wallets
- Private keys and other sensitive information are stored online, making them more vulnerable to hacks and theft
- More susceptible to malware and phishing attacks
How to Protect Your Hardware Wallet
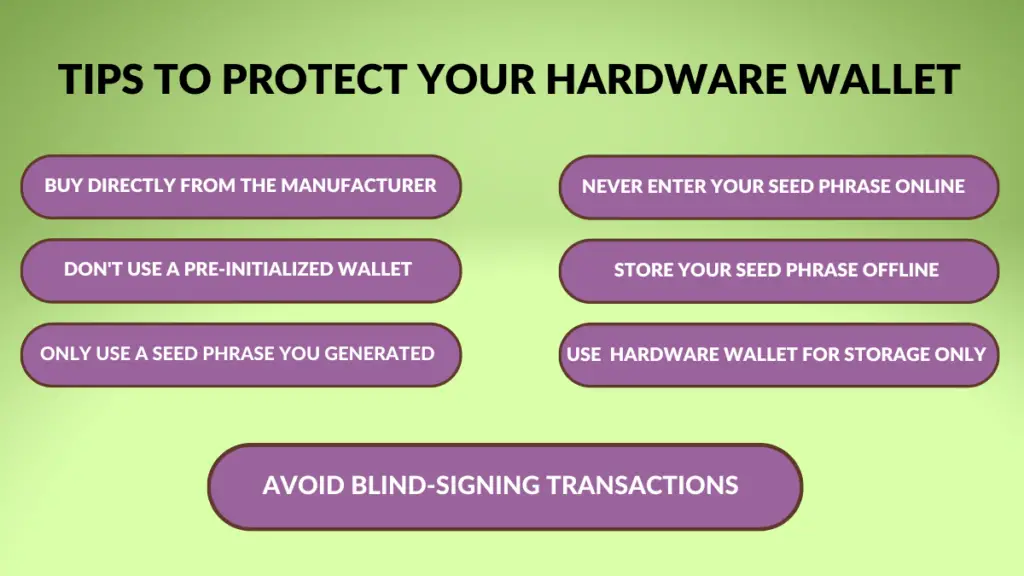
Protecting your hardware wallet begins before you even buy it. Here are some tips to protect your hardware wallet.
Purchase your hardware wallet directly from the manufacturer
It’s important to ensure your hardware wallet hasn’t been tampered with or compromised in any way. To avoid this, I recommend buying your hardware wallet directly from the manufacturer’s website or from an authorized reseller.
This reduces the risk of receiving a counterfeit or tampered device, which can compromise the security of your wallet and lead to the loss of your funds.
Don’t let the cheaper prices of third-party sellers fool you!
Some third-party sellers may offer hardware wallets at a lower price than the manufacturer, but they could potentially be selling tampered or counterfeit devices. These devices may have hidden vulnerabilities or malware that could be used to steal your private keys and funds.
Don’t use a pre-initialized hardware wallet
Initializing a hardware wallet yourself ensures that you are the only person with access to the device’s private keys. This reduces the risk of theft and assures that you have complete control over your funds.
Additionally, initializing your own hardware wallet is a simple and straightforward process that takes only a few minutes.
So, how can you tell if your wallet has been pre-initialized?
If your device doesn’t require you to generate, record, and verify a secret recovery phrase, it’s likely been previously set up by someone else. Another red flag is that your wallet only requires you to set a PIN, which means the seed phrase has previously been generated.
If you notice any of these red flags, do not use the wallet. Rather, return it and either request a different device (assuming you got it from the manufacturer) or shop elsewhere.
Only use a seed phrase you generated
Never use a wallet that comes with the seed phrase pre-generated. This means someone else knows the phrase and has access to your wallet and your funds. You can create a new wallet with a new seed phrase, but you still run the risk of the device having other malicious qualities to it.
It’s always best to get a new device if yours has been compromised. Especially if it shows up at your front door compromised!
Never enter your recovery phrase on any computer or smartphone
Hardware wallets are secure because they operate offline. Hence, entering your recovery phrase on your computer or mobile device defeats its purpose. For example, entering your seed phrase into a wallet like MetaMask puts your hardware device at risk.
To ensure your crypto assets remain safe, you should only use your hardware wallet offline or through the wallet’s app (such as Ledger Live for Ledger wallets).
Store your recovery phrase offline
Never store your secret recovery phrase online. This includes your computer, phone, or any other device that’s connected to the internet. Always store your seed phrase in a physical and secure location. Storing it online leaves it susceptible to hackers.
Here’s where not to store your recovery phrase:
- Your mobile phone (including photos, files, and apps)
- Your computer (hard drive, files, software)
- A cloud (such as cloud storage like iCloud)
- Encrypted storage
Write it down, and keep it offline. It’s that simple.
Use your hardware wallet for storage, not transacting
So your goal is to use a hardware wallet to protect all your precious digital assets, right? Then make sure to use a dedicated device solely for storing your assets. Never use your storage wallet as a transaction wallet.
Every time you interact with a platform, your wallet is at risk. This includes connecting to websites, signing for transactions, and interacting with malicious or fake assets sent to your wallet.
The only transactions that should occur on your storage wallet are transfers. For example, if you want to sell an asset, such as an NFT, transfer it from your hardware wallet to your ‘transaction wallet’ to sell it.
A transaction wallet is nothing more than a wallet you use to execute transactions and connect to decentralized apps (dapps), along with other high-risk actions. You can use any software wallet like MetaMask as your transaction wallet.
This will ensure your device isn’t exposed to any malicious websites.
Don’t ‘blind-sign’ a transaction
Blind signing is when you approve a transaction using your wallet without knowing the full details of what you’re signing. This is dangerous because you could be giving a scammer access to your wallet and all of your funds. That’s why you should avoid blind signing at all costs.
That said, certain decentralized platforms require you to enable blind signing to execute transactions. That means you simply trust without verifying—which is a huge risk.
This is a perfect example of why you should never sign transactions using a wallet that holds your assets. Use a dedicated transaction wallet.
Frequently Asked Questions
How do hardware wallets work?
Hardware wallets use a physical device to store private keys and sign transactions offline, keeping your crypto assets secure from online threats.
Where should I buy a hardware wallet?
You can buy hardware wallets from their official websites or authorized resellers. Avoid third-party sellers to ensure the authenticity of the device.
Which is the safest hardware wallet?
The safest hardware wallets have secure elements and are well-reviewed. Ledger and Trezor are the two most trusted hardware wallet brands. There are other factors to consider when choosing a device though.
How long do hardware wallets last?
Hardware wallets typically last for years, and their lifespan can be extended with proper care. The battery is usually the first to fail. Some brands like Ledger and Trezor offer warranties of up to 2 years.

1 thought on “Can Hardware Wallets Be Hacked? (Yes, Here’s How)”
Comments are closed.